Rootkit
A root kit is a collection of computer software, typically malicious, designed to enable access to a computer or areas of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software.[1] The term rootkit is aconcatenation of "root" (the traditional name of the privileged account on Unix-likeoperating systems) and the word "kit" (which refers to the software components that implement the tool). The term "rootkit" has negative connotations through its association with malware.[1]
Rootkit installation can be automated, or anattacker can install it after having obtained root or Administrator access. Obtaining this access is a result of direct attack on a system, i.e. exploiting a known vulnerability (such asprivilege escalation) or a password (obtained by cracking or social engineering tactics like "phishing"). Once installed, it becomes possible to hide the intrusion as well as to maintain privileged access. The key is the root or administrator access. Full control over a system means that existing software can be modified, including software that might otherwise be used to detect or circumvent it.
Rootkit detection is difficult because a rootkit may be able to subvert the software that is intended to find it. Detection methods include using an alternative and trusted operating system, behavioral-based methods, signature scanning, difference scanning, and memory dump analysis. Removal can be complicated or practically impossible, especially in cases where the rootkit resides in the kernel; reinstallation of the operating system may be the only available solution to the problem.[2]When dealing with firmware rootkits, removal may require hardware replacement, or specialized equipment.
History
The term rootkit or root kit originally referred to a maliciously modified set of administrative tools for a Unix-like operating system that granted "root" access.[3] If an intruder could replace the standard administrative tools on a system with a rootkit, the intruder could obtain root access over the system whilst simultaneously concealing these activities from the legitimatesystem administrator. These first-generation rootkits were trivial to detect by using tools such as Tripwire that had not been compromised to access the same information.[4][5] Lane Davis and Steven Dake wrote the earliest known rootkit in 1990 forSun Microsystems' SunOS UNIX operating system.[6] In the lecture he gave upon receiving the Turing award in 1983, Ken Thompson of Bell Labs, one of the creators ofUnix, theorized about subverting the C compiler in a Unix distribution and discussed the exploit. The modified compiler would detect attempts to compile the Unix
logincommand and generate altered code that would accept not only the user's correct password, but an additional "backdoor" password known to the attacker. Additionally, the compiler would detect attempts to compile a new version of the compiler, and would insert the same exploits into the new compiler. A review of the source code for the login command or the updated compiler would not reveal any malicious code.[7] This exploit was equivalent to a rootkit.
The first documented computer virus to target the personal computer, discovered in 1986, used cloaking techniques to hide itself: theBrain virus intercepted attempts to read theboot sector, and redirected these to elsewhere on the disk, where a copy of the original boot sector was kept.[1] Over time,DOS-virus cloaking methods became more sophisticated, with advanced techniques including the hooking of low-level disk INT 13H BIOS interrupt calls to hide unauthorized modifications to files.[1]
The first malicious rootkit for the Windows NToperating system appeared in 1999: a trojan called NTRootkit created by Greg Hoglund.[8] It was followed by HackerDefender in 2003.[1]The first rootkit targeting Mac OS X appeared in 2009,[9] while the Stuxnet worm was the first to target programmable logic controllers(PLC).[10]
Sony BMG copy protection rootkit scandal
Screenshot of RootkitRevealer, showing the files hidden by theExtended Copy Protection rootkit
In 2005, Sony BMG published CDs with copy protection and digital rights managementsoftware called Extended Copy Protection, created by software company First 4 Internet. The software included a music player but silently installed a rootkit which limited the user's ability to access the CD.[11] Software engineer Mark Russinovich, who created the rootkit detection tool RootkitRevealer, discovered the rootkit on one of his computers.[1] The ensuing scandal raised the public's awareness of rootkits.[12] To cloak itself, the rootkit hid from the user any file starting with "$sys$". Soon after Russinovich's report, malware appeared which took advantage of that vulnerability of affected systems.[1] One BBC analyst called it a "public relations nightmare."[13] Sony BMG releasedpatches to uninstall the rootkit, but it exposed users to an even more serious vulnerability.[14]The company eventually recalled the CDs. In the United States, a class-action lawsuit was brought against Sony BMG.[15]
Greek wiretapping case 2004–05
The Greek wiretapping case of 2004-05, also referred to as Greek Watergate,[16] involved the illegal telephone tapping of more than 100 mobile phones on the Vodafone Greecenetwork belonging mostly to members of theGreek government and top-ranking civil servants. The taps began sometime near the beginning of August 2004 and were removed in March 2005 without discovering the identity of the perpetrators. The intruders installed a rootkit targeting Ericsson's AXE telephone exchange. According to IEEE Spectrum, this was "the first time a rootkit has been observed on a special-purpose system, in this case an Ericsson telephone switch."[17] The rootkit was designed to patch the memory of the exchange while it was running, enablewiretapping while disabling audit logs, patch the commands that list active processes and active data blocks, and modify the data blockchecksum verification command. A "backdoor" allowed an operator withsysadmin status to deactivate the exchange's transaction log, alarms and access commands related to the surveillance capability.[17] The rootkit was discovered after the intruders installed a faulty update, which caused SMS texts to be undelivered, leading to an automated failure report being generated. Ericsson engineers were called in to investigate the fault and discovered the hidden data blocks containing the list of phone numbers being monitored, along with the rootkit and illicit monitoring software.
Uses
Modern rootkits do not elevate access,[3] but rather are used to make another software payload undetectable by adding stealth capabilities.[8] Most rootkits are classified asmalware, because the payloads they are bundled with are malicious. For example, a payload might covertly steal user passwords,credit card information, computing resources, or conduct other unauthorized activities. A small number of rootkits may be considered utility applications by their users: for example, a rootkit might cloak a CD-ROM-emulation driver, allowing video game users to defeatanti-piracy measures that require insertion of the original installation media into a physical optical drive to verify that the software was legitimately purchased.
Rootkits and their payloads have many uses:
- Provide an attacker with full access via abackdoor, permitting unauthorized access to, for example, steal or falsify documents. One of the ways to carry this out is to subvert the login mechanism, such as the /bin/login program on Unix-like systems orGINA on Windows. The replacement appears to function normally, but also accepts a secret login combination that allows an attacker direct access to the system with administrative privileges, bypassing standard authentication andauthorization mechanisms.
- Conceal other malware, notably password-stealing key loggers and computer viruses.[18]
- Appropriate the compromised machine as azombie computer for attacks on other computers. (The attack originates from the compromised system or network, instead of the attacker's system.) "Zombie" computers are typically members of largebotnets that can launch denial-of-service attacks, distribute e-mail spam, conductclick fraud, etc.
- Enforcement of digital rights management(DRM).
In some instances, rootkits provide desired functionality, and may be installed intentionally on behalf of the computer user:
- Conceal cheating in online games from software like Warden.[19]
- Detect attacks, for example, in ahoneypot.[20]
- Enhance emulation software and security software.[21] Alcohol 120% and Daemon Tools are commercial examples of non-hostile rootkits used to defeat copy-protection mechanisms such as SafeDiscand SecuROM. Kaspersky antivirus software also uses techniques resembling rootkits to protect itself from malicious actions. It loads its own drivers to intercept system activity, and then prevents other processes from doing harm to itself. Its processes are not hidden, but cannot be terminated by standard methods (It can be terminated with Process Hacker).
- Anti-theft protection: Laptops may have BIOS-based rootkit software that will periodically report to a central authority, allowing the laptop to be monitored, disabled or wiped of information in the event that it is stolen.[22]
- Bypassing Microsoft Product Activation[23]
Types
There are at least five types of rootkit, ranging from those at the lowest level in firmware (with the highest privileges), through to the least privileged user-based variants that operate in Ring 3. Hybrid combinations of these may occur spanning, for example, user mode and kernel mode.[24]
User mode
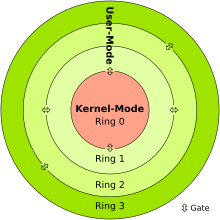
Computer security rings (Note thatRing ‑1 is not shown)
User-mode rootkits run in Ring 3, along with other applications as user, rather than low-level system processes.[25] They have a number of possible installation vectors to intercept and modify the standard behavior of application programming interfaces (APIs). Some inject a dynamically linked library (such as a .DLL file on Windows, or a .dylib file on Mac OS X) into other processes, and are thereby able to execute inside any target process to spoof it; others with sufficient privileges simply overwrite the memory of a target application. Injection mechanisms include:[25]
- Use of vendor-supplied application extensions. For example, Windows Explorerhas public interfaces that allow third parties to extend its functionality.
- Interception of messages.
- Debuggers.
- Exploitation of security vulnerabilities.
- Function hooking or patching of commonly used APIs, for example, to hide a running process or file that resides on a filesystem.[26]
Kernel mode
Kernel-mode rootkits run with the highest operating system privileges (Ring 0) by adding code or replacing portions of the core operating system, including both the kerneland associated device drivers. Most operating systems support kernel-mode device drivers, which execute with the same privileges as the operating system itself. As such, many kernel-mode rootkits are developed as device drivers or loadable modules, such as loadable kernel modules in Linux or device drivers inMicrosoft Windows. This class of rootkit has unrestricted security access, but is more difficult to write.[27] The complexity makes bugs common, and any bugs in code operating at the kernel level may seriously impact system stability, leading to discovery of the rootkit.[27] One of the first widely known kernel rootkits was developed for Windows NT 4.0 and released in Phrack magazine in 1999 by Greg Hoglund.[28][29][30] Kernel rootkits can be especially difficult to detect and remove because they operate at the samesecurity level as the operating system itself, and are thus able to intercept or subvert the most trusted operating system operations. Any software, such as antivirus software, running on the compromised system is equally vulnerable.[31] In this situation, no part of the system can be trusted.
A rootkit can modify data structures in the Windows kernel using a method known asdirect kernel object manipulation (DKOM).[32]This method can be used to hide processes. A kernel mode rootkit can also hook the System Service Descriptor Table (SSDT), or modify the gates between user mode and kernel mode, in order to cloak itself.[3] Similarly for the Linux operating system, a rootkit can modify the system call table to subvert kernel functionality.[33] It's common that a rootkit creates a hidden, encrypted filesystem in which it can hide other malware or original copies of files it has infected.[34] Operating systems are evolving to counter the threat of kernel-mode rootkits. For example, 64-bit editions of Microsoft Windows now implement mandatory signing of all kernel-level drivers in order to make it more difficult for untrusted code to execute with the highest privileges in a system.[35]
Bootkits
A kernel-mode rootkit variant called a bootkitcan infect startup code like the Master Boot Record (MBR), Volume Boot Record (VBR) orboot sector, and in this way can be used to attack full disk encryption systems.
An example of such an attack on disk encryption is the "evil maid attack", in which an attacker installs a bootkit on an unattended computer. The envisioned scenario is a maid sneaking in the hotel room where the victims left their hardware.[36] The bootkit replaces the legitimate boot loaderwith one under their control. Typically the malware loader persists through the transition to protected mode when the kernel has loaded, and is thus able to subvert the kernel.[37][38][39] For example, the "Stoned Bootkit" subverts the system by using a compromised boot loader to intercept encryption keys and passwords.[40] More recently, the Alureon rootkit has successfully subverted the requirement for 64-bit kernel-mode driver signing in Windows 7 by modifying the master boot record.[41]Although not malware in the sense of doing something the user doesn't want, certain "Vista Loader" or "Windows Loader" software works in a similar way by injecting an ACPISLIC (System Licensed Internal Code) table in the RAM-cached version of the BIOS during boot, in order to defeat the Windows Vista and Windows 7 activation process.[42][43] This vector of attack was rendered useless in the (non-server) versions of Windows 8, which use a unique, machine-specific key for each system, that can only be used by that one machine.[44] Many antivirus companies provide free utilities and programs to remove bootkits.
Hypervisor level
Rootkits have been created as Type IIHypervisors in academia as proofs of concept. By exploiting hardware virtualization features such as Intel VT or AMD-V, this type of rootkit runs in Ring -1 and hosts the target operating system as a virtual machine, thereby enabling the rootkit to intercept hardware calls made by the original operating system.[5] Unlike normal hypervisors, they do not have to load before the operating system, but can load into an operating system before promoting it into a virtual machine.[5] A hypervisor rootkit does not have to make any modifications to the kernel of the target to subvert it; however, that does not mean that it cannot be detected by the guest operating system. For example, timing differences may be detectable in CPU instructions.[5] The "SubVirt" laboratory rootkit, developed jointly by Microsoft and University of Michiganresearchers, is an academic example of a virtual machine–based rootkit (VMBR),[45]while Blue Pill software is another. In 2009, researchers from Microsoft and North Carolina State University demonstrated a hypervisor-layer anti-rootkit called Hooksafe, which provides generic protection against kernel-mode rootkits.[46] Windows 10introduced a new feature called "Device Guard", that takes advantage of virtualization to provide independent external protection of an operating system against rootkit-type malware.[47]
Firmware and hardware
A firmware rootkit uses device or platform firmware to create a persistent malware image in hardware, such as a router, network card,[48] hard drive, or the system BIOS.[25][49]The rootkit hides in firmware, because firmware is not usually inspected for code integrity. John Heasman demonstrated the viability of firmware rootkits in both ACPIfirmware routines[50] and in a PCI expansion card ROM.[51] In October 2008, criminals tampered with European credit card-reading machines before they were installed. The devices intercepted and transmitted credit card details via a mobile phone network.[52] In March 2009, researchers Alfredo Ortega and Anibal Sacco published details of a BIOS-level Windows rootkit that was able to survive disk replacement and operating system re-installation.[53][54][55] A few months later they learned that some laptops are sold with a legitimate rootkit, known as AbsoluteCompuTrace or Absolute LoJack for Laptops, preinstalled in many BIOS images. This is an anti-theft technology system that researchers showed can be turned to malicious purposes.[22]
Intel Active Management Technology, part ofIntel vPro, implements out-of-band management, giving administrators remote administration, remote management, andremote control of PCs with no involvement of the host processor or BIOS, even when the system is powered off. Remote administration includes remote power-up and power-down, remote reset, redirected boot, console redirection, pre-boot access to BIOS settings, programmable filtering for inbound and outbound network traffic, agent presence checking, out-of-band policy-based alerting, access to system information, such as hardware asset information, persistent event logs, and other information that is stored in dedicated memory (not on the hard drive) where it is accessible even if the OS is down or the PC is powered off. Some of these functions require the deepest level of rootkit, a second non-removable spy computer built around the main computer. Sandy Bridge and future chipsets have "the ability to remotely kill and restore a lost or stolen PC via 3G". Hardware rootkits built into the chipset can help recover stolen computers, remove data, or render them useless, but they also present privacy and security concerns of undetectable spying and redirection by management or hackers who might gain control.
Installation and cloaking
Rootkits employ a variety of techniques to gain control of a system; the type of rootkit influences the choice of attack vector. The most common technique leverages security vulnerabilities to achieve surreptitiousprivilege escalation. Another approach is to use a Trojan horse, deceiving a computer user into trusting the rootkit's installation program as benign—in this case, social engineeringconvinces a user that the rootkit is beneficial.[27] The installation task is made easier if the principle of least privilege is not applied, since the rootkit then does not have to explicitly request elevated (administrator-level) privileges. Other classes of rootkits can be installed only by someone with physical access to the target system. Some rootkits may also be installed intentionally by the owner of the system or somebody authorized by the owner, e.g. for the purpose of employee monitoring, rendering such subversive techniques unnecessary.[56] The installation of malicious rootkits is commercially driven, with a pay-per-install (PPI) compensation method typical for distribution.[57][58]
Once installed, a rootkit takes active measures to obscure its presence within the host system through subversion or evasion of standard operating system security tools andapplication programming interface (APIs) used for diagnosis, scanning, and monitoring. Rootkits achieve this by modifying the behavior of core parts of an operating systemthrough loading code into other processes, the installation or modification of drivers, orkernel modules. Obfuscation techniques include concealing running processes from system-monitoring mechanisms and hiding system files and other configuration data.[59]It is not uncommon for a rootkit to disable theevent logging capacity of an operating system, in an attempt to hide evidence of an attack. Rootkits can, in theory, subvert anyoperating system activities.[60] The "perfect rootkit" can be thought of as similar to a "perfect crime": one that nobody realizes has taken place. Rootkits also take a number of measures to ensure their survival against detection and "cleaning" by antivirus software in addition to commonly installing into Ring 0 (kernel-mode), where they have complete access to a system. These includepolymorphism (changing so their "signature" is hard to detect), stealth techniques, regeneration, disabling or turning off anti-malware software.[61] and not installing onvirtual machines where it may be easier for researchers to discover and analyze them.
Comments
Post a Comment